Our VPN leak test tool checks if your VPN is leaking by running tests in a browser, and separately via your torrent client.
Below is more information on how the tool works to test for different types of leaks.
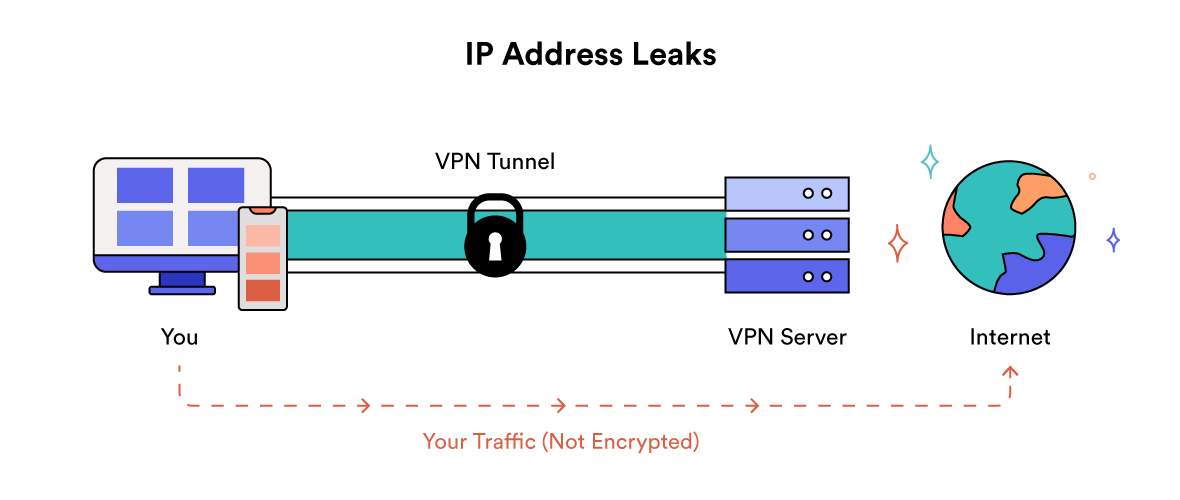
IPv4/IPv6
Our tool first detects your public IPv4 and IPv6 address before you connect to a VPN, and then again once connected.
The tool then compares the two sets of IP addresses. If they’re different then there is no IP leak.
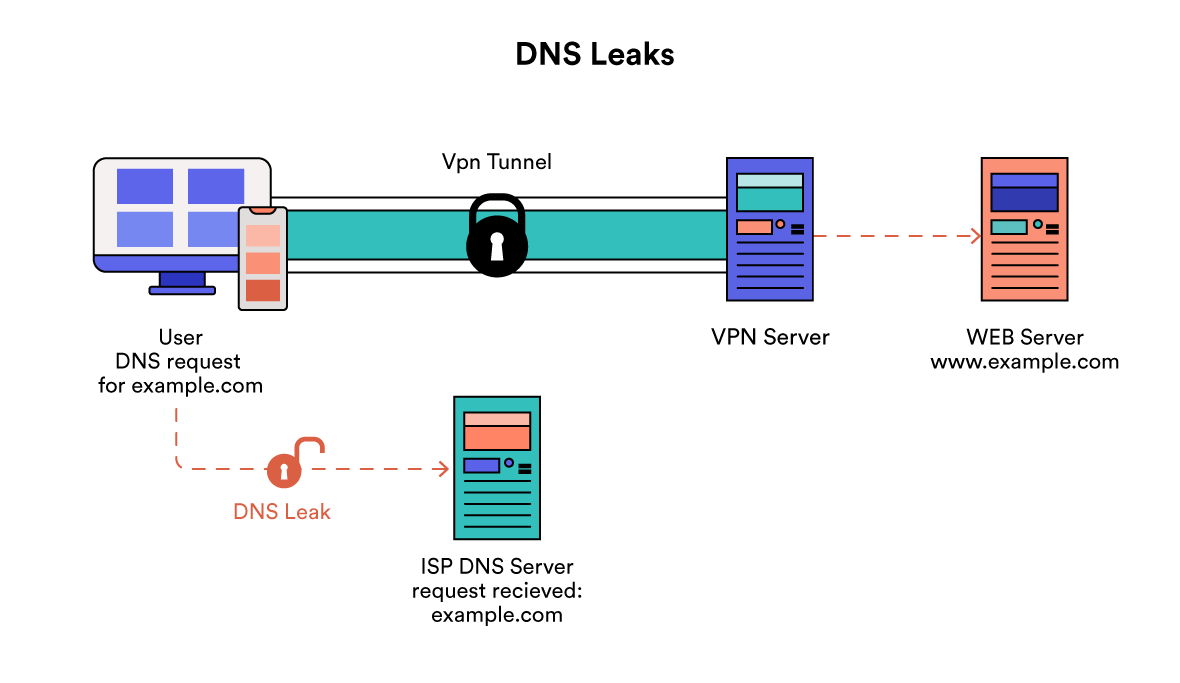
DNS
Our tool makes a DNS request for a unique hostname in your browser when your VPN isn’t running.
That hostname points at DNS servers hosted by us, and we log all the IPs that contact our server using that unique hostname.
The tool then repeats this process once you turn your VPN on.
The IPs that we see are the DNS servers that your browser is using, and we map these to the organization that owns those IPs.
If the organization is the same both before and after you turn on your VPN, then the tool will warn you of a DNS leak.
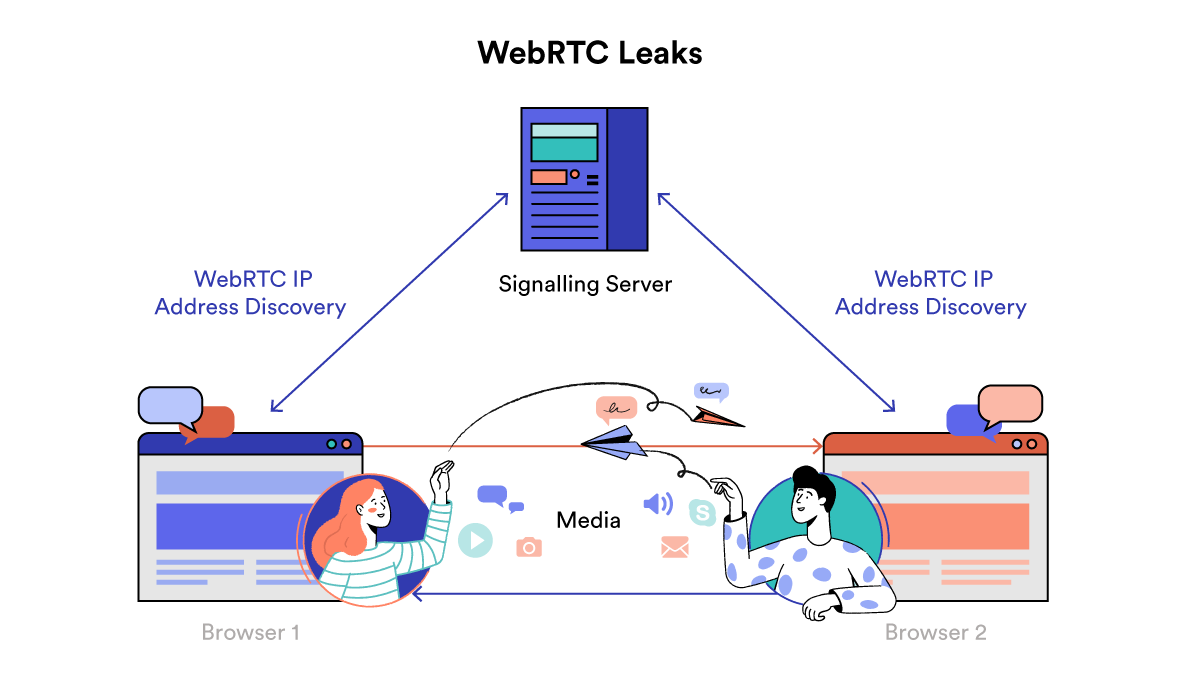
WebRTC
To detect a WebRTC leak we use JavaScript to create a peer-to-peer connection via your browser, utilizing the WebRTC API built into your browser.
The WebRTC API allows us to make STUN requests, which return both the public and local IP addresses for the browser, which JavaScript can then read.
If the connection is successful, and the IP address listed is your own, then there’s a leak.
However, if the IP address listed is not your own, then everything is fine.
HTML5 Geolocation
Your HTML5 geolocation closely mirrors your actual physical location.
This geolocation information is collected and made available via an API in your web browser.
Our tool asks for permission to access this data – if you grant our tool access, it can check your HTML5 geolocation and compare it to your IP address location.
If your IP and HTML5 locations aren’t a close match, there’s a chance websites and services will know you’re not really where your VPN server is.
Flash Player
Flash Player is an extreme security risk, and has now been officially discontinued.
Our tool runs a Javascript command to check a list of plugins running in your browser. If Flash is listed, then the tool warns you to disable it.
Tor Exit Node
Certain IP addresses are registered as exit nodes on the Tor network. These IP addresses are publicly known and listed.
Our tool cross-references your IP address with a database of all known Tor exit nodes, and tells you whether or not it appears on it.
Data Center IP Address
Some IP addresses are classified as data center IPs, rather than residential IPs.
Our tool cross-references your IP address with a database of known data center IPs, and tells you whether or not it’s listed on it.
Data center IP addresses are commonly associated with VPNs. Therefore, this result is highly likely to come back as positive.